Detect Ransomware, Malware, and Corruption.
Get One Click Recoveries. End Recovery Anxiety.
Built on AWS for AWS, Elastio is purpose built for the cloud. From creating your tenant to being up and running takes most customers only 15 minutes. It doesn’t require specialized talent or a heavy lift from your team to run on a day-to-day basis. And best of all, with our global compression and deduplication, many Elastio customers find that the platform pays for itself.
Elastio secures all data inside customer designated AWS accounts separated from the production accounts. Data is never transferred to or accessible by Elastio.
Data is encrypted at-rest using your Amazon KMS keys, encrypted in-flight, and can be air-gapped in a separate account as an additional layer of defense. It is easily deployed as a CloudFormation Stack in your account.
We enable S3 server-side-encryption (SSE) as an additional layer of protection. Before being uploaded to S3, all client-side backup data is encrypted with a unique AES key for every asset. Additionally, these keys are protected by a per-vault KMS key, so only IAM roles with access permissions are able to decrypt data in the vault.
Because Elastio uses unique AES keys for each asset, our platform ensures that even a malicious client with knowledge of one encryption key is prevented from accessing the backup data of any other asset.
Built as a microservice on SQS queues and Lambda functions, Elastio uses a lightweight command-and-control pathway between our SaaS/Servers? and customer AWS accounts. Though our service requires access to certain AWS APIs, this can be accomplished via PrivateLink if the VPC is isolated from the internet. During the service deployment, the customer grants permission to an Elastio-controlled, tenant-specific IAM role that deploys the service, reads the queues and invokes the lambdas. Customers can monitor activity within these resources and rest assured that only the specific operations granted to our IAM role will be performed. There is never an IP-network link between Elastio and the customer’s VPCs; all communication is via SQS messages and Lambda invocations.
Elastio’s self-sufficient service does not depend on the tenant, and it performs its own backup scheduling. Customers can use our CLI (run within an Elastio service account) to list local recovery points and initiate restores. This ensures that an Elastio outage won’t stop scheduled backups from taking place or prevent customers from deploying backup restorations.
Elastio stores data in a deduplicated, compressed form, and tracks everything under protection: files, databases, tables, partitions and block devices. Incremental backups optimize performance and space efficiency. Multiple workflows can also access the data concurrently.
Our backups are incremental forever for performance and cost efficiency.
Elastio’s storage service primarily uses server-less technologies like Lambda and DynamoDB. Our storage service, ScaleZ™, is engineered to run on ephemeral Spot instances. This helps us lower costs we can pass on as savings to our customers.
Elastio scales-out based on workload size, scales-up as needed for concurrent data access, and automatically scales-to-zero when the job is complete.
We enable S3 server-side-encryption (SSE) as an additional layer of protection. Before being uploaded to S3, all client-side backup data is encrypted with a unique AES key for every asset. Additionally, these keys are protected by a per-vault KMS key, so only IAM roles with access permissions are able to decrypt data in the vault.
Because Elastio uses unique AES keys for each asset, our platform ensures that even a malicious client with knowledge of one encryption key is prevented from accessing the backup data from any other asset.
Backup data are organized into vaults, each with a separate S3 bucket with a dedicated KMS key that encrypts all data and operates in a specific VPC. Every vault is a separate deduplication domain with a dedicated key, making it easy to compartmentalize and secure sensitive data while also reducing storage costs.
A simple CLI command in a terminal or a script keeps streams, files, block devices, databases and tables protected and recoverable on-demand. Integrates with serverless compute, containers, VMs and any Windows or Linux machine.
Elastio can agentlessly inspect, protect, and restore entire EC2 instances or specific EBS volumes, making it convenient and easy to deploy. VSS is also supported for Windows EC2 instances.
Scales-out based on workload size, scales-up on demand for concurrent data access, and automatically scales-to-zero when the job is complete.
For shorter recovery point objectives (RPO) and faster recovery time objectives (RTO), or those needing more flexibility in backup and cyber recovery options, Elastio offers host-based change-block tracking, backup and cyber recovery capability for Windows and Linux. We even inspect and back-up high-speed ephemeral direct-attached NVMe storage on AWS i3, m5d, m6d, and other Nitro-instance types with local storage options.
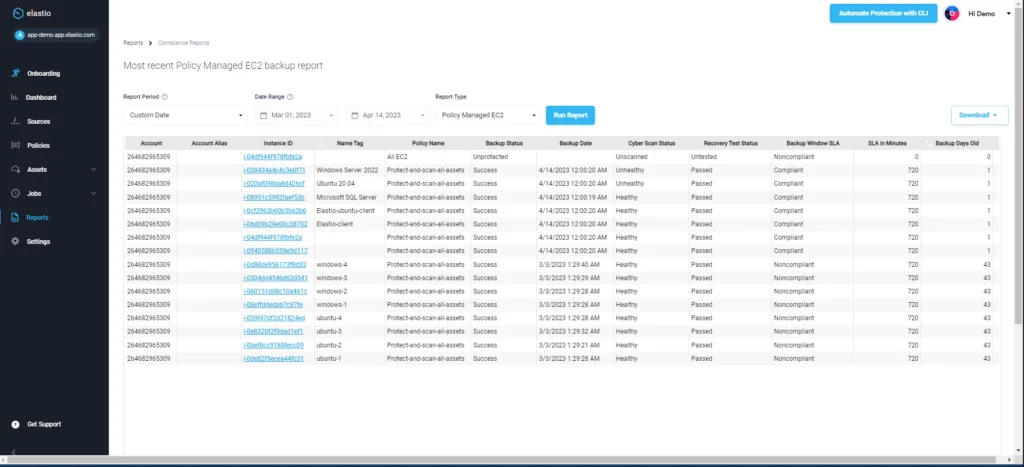
Recovery points can be retained forever and customized for every compliance use case.
Agentless and host-based EC2, EBS and block backups can be mounted in seconds. Quickly surfacing the underlying file system speeds up database and file recoveries, and enables applications direct access to data. EBS backups can be mounted on local workstations to gain access to individual files and folders.
Automatically replicates backups between regions for disaster recovery protection.
Elastio is built to leverage AWS native services, with automated detection and protection orchestrated into the platform. This ensures every asset is protected, stays compliant and remains recoverable without needing manual configurations or management.
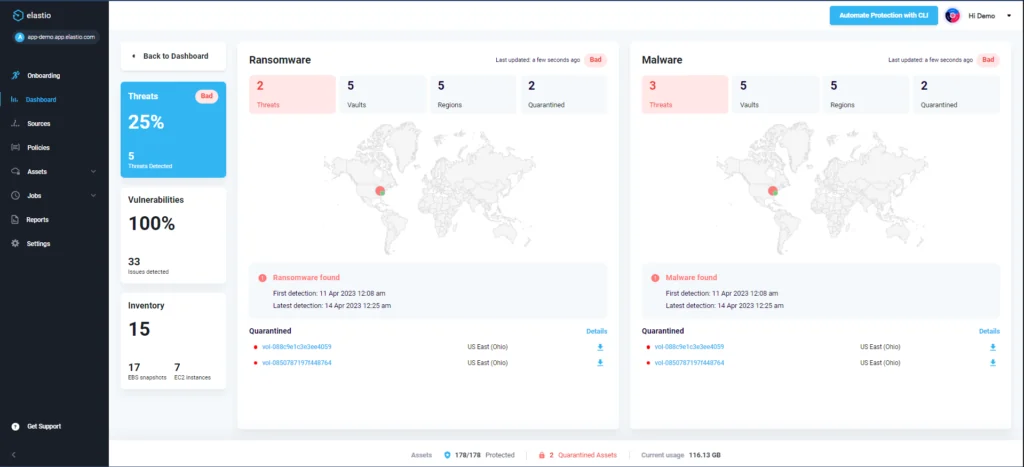
Elastio’s ML-powered ransomware detection applies signature analysis, deterministic analysis and malware scanning to each backup. The platform alerts and quarantines suspicious backups, allowing teams to rapidly recover applications and data to the last known clean backup. Learn more
The Elastio ScaleZ™ Vault service is secured in the customer AWS account. SafetyLock™ protects the perimeter of the vault, while AWS ObjectLock prevents deletion. SafetyLock™ integrates ObjectLock into Elastio’s retention algorithms to ensure vaults remain secure from both malicious actors and human error.
SoftDelete protects Tenant APIs in the same way as KMS key deletion works. SoftDelete will not delete the vault for 30 days and sends alerts when a deletion has been completed.
Manage protection of assets across all accounts from one place with consistent tooling, one set of policies, and Elastio integrations into CI/CD pipelines.
Assign permissions to users based on their roles within a Tenant. Elastio offers a simple, manageable approach to Tenant access management that is less error-prone than individually assigning user permissions.
Deploy the Elastio service securely into your AWS account in a few minutes.
Fully leverage the API with its data protection capabilities for protecting, restoring and accessing copies of data from deployment scripts or from within an application.
Our cloud operations team continuously monitors the health of all customers and proactively resolves issues and alerts customers to operating issues. Platform updates are automatically deployed including ransomware and malware databases.
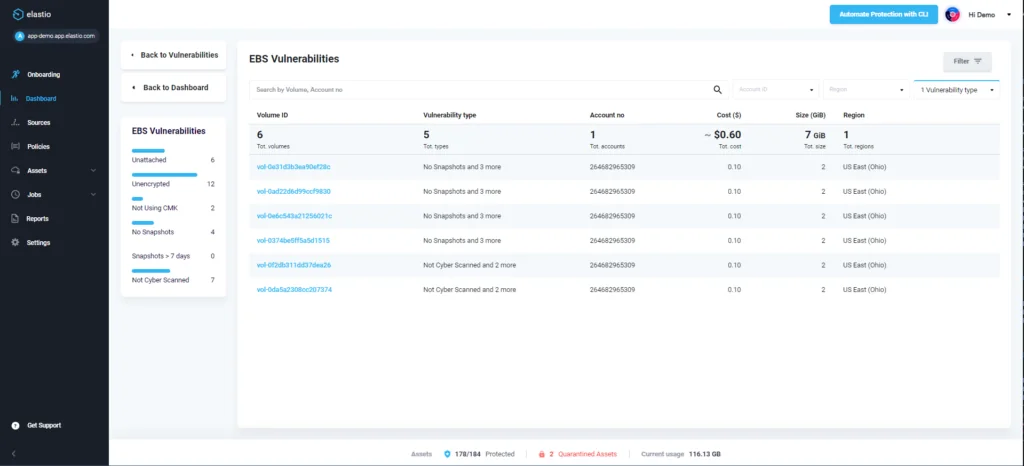
Backup tools don’t discriminate between good data and compromised data. They simply take a snapshot. For three out of four businesses, there’s a good chance those backups contain ransomware, malware, or corruption. This allows threats to not only make an appearance in backup after backup, but also to permeate your infrastructure and make recoveries difficult – if not impossible.
Elastio integrates with AWS Backup to continuously scan your backup data for threats, recovery tests your backups to ensure a successful restoration, and quickly identifies the last clean recovery point. So you can get back to being an IT superhero

Detect, quarantine, and respond to unseen threats within your AWS backup data to streamline the recovery process.

Eliminate unseen threats and successfully recover from "predictable" disasters and unpredictable cyber attacks.

Elevate your compliance and risk posture through comprehensive reporting and advanced analytics based on insightful AI/ML.
If you’re ready to go from recovery anxiety to assured recovery, let us show you what Elastio can do for your organization.

The first time backups are tested is often at the point of recovery—when the pressure is on. A trial-and-error process ensues, resulting in excess downtime.
Elastio is flipping the script on this process. By ensuring your backups are recovery tested and scanned for threats at the point of creation, you’ll not only meet your RTO and RPO objectives—you’ll exceed them.












Read our latest blogs about ransomware, cyber recovery, and more.