Elastio Platform
We enable organizations to verify data integrity in near real-time, enabling clean recovery from any attack with minimal downtime and data loss
Why Elastio?
Differentiators
Detects ransomware encryption
Low false positive rate
Stays ahead of
emerging threats
Cannot be bypassed
Multi-platform & multi-backup


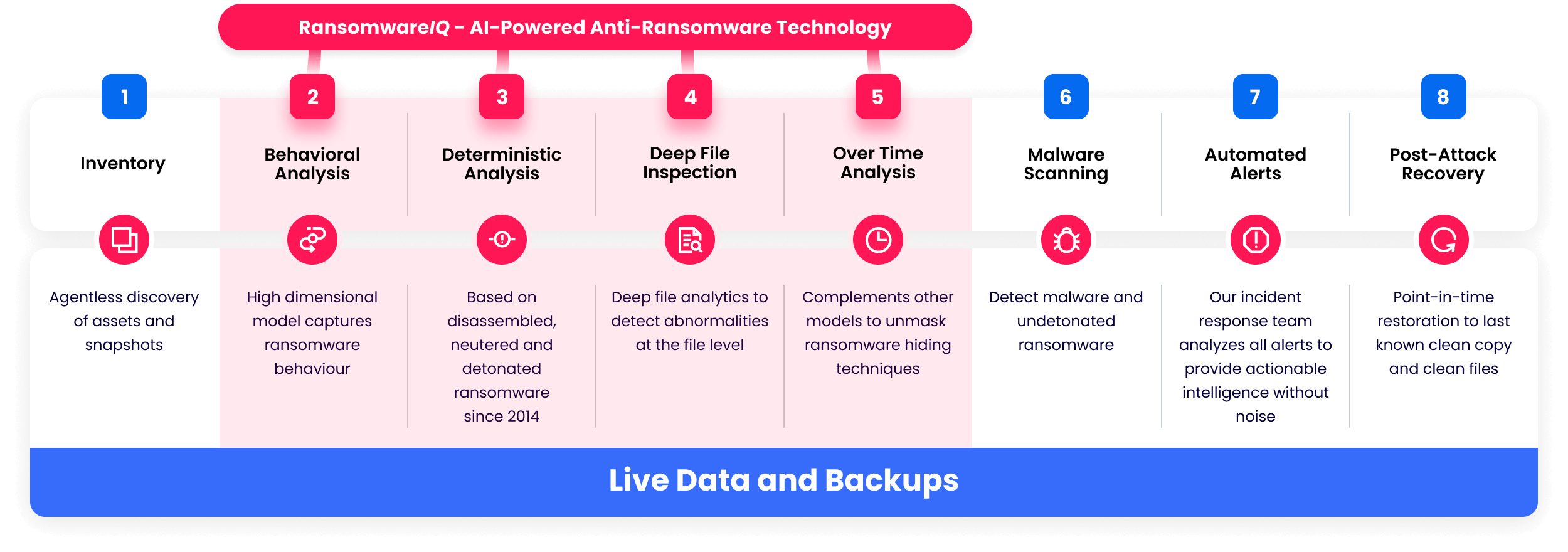
Our AI/ML engine leverages deep ransomware research and over-time analysis to go beyond anomaly detection and precisely identify ransomware encryption in your data

Single-digit false positives across 25 million file inspections prevent alert fatigue

Uses advanced statistical and behavioral modeling to detect novel threats that have not hit the market with 99.99% accuracy

Operating agentlessly, Elastio inspects snapshots and backups outside the control of any malware-infected endpoint, enabling it to unmask any ransomware-hiding techniques

Elastio integrates seamlessly with existing backup vendors and works across multi-cloud, hybrid, and on-premise environments
Others
EDR/XDR, AV Scanners,
Backup Providers

Traditional methods that rely on anomaly detection are ineffective against modern ransomware tactics that have evolved to stay undetected

Anomaly detection solutions have very high false positive rates, leading to alerts being ignored or disabled

Performs scans against a library of known signatures so are unable to detect novel threats

Agent-based ransomware protection solutions are easily unhooked and bypassed by modern ransomware

Backup providers are silos and do not provide uniform security functionality across all environments
How Elastio Works
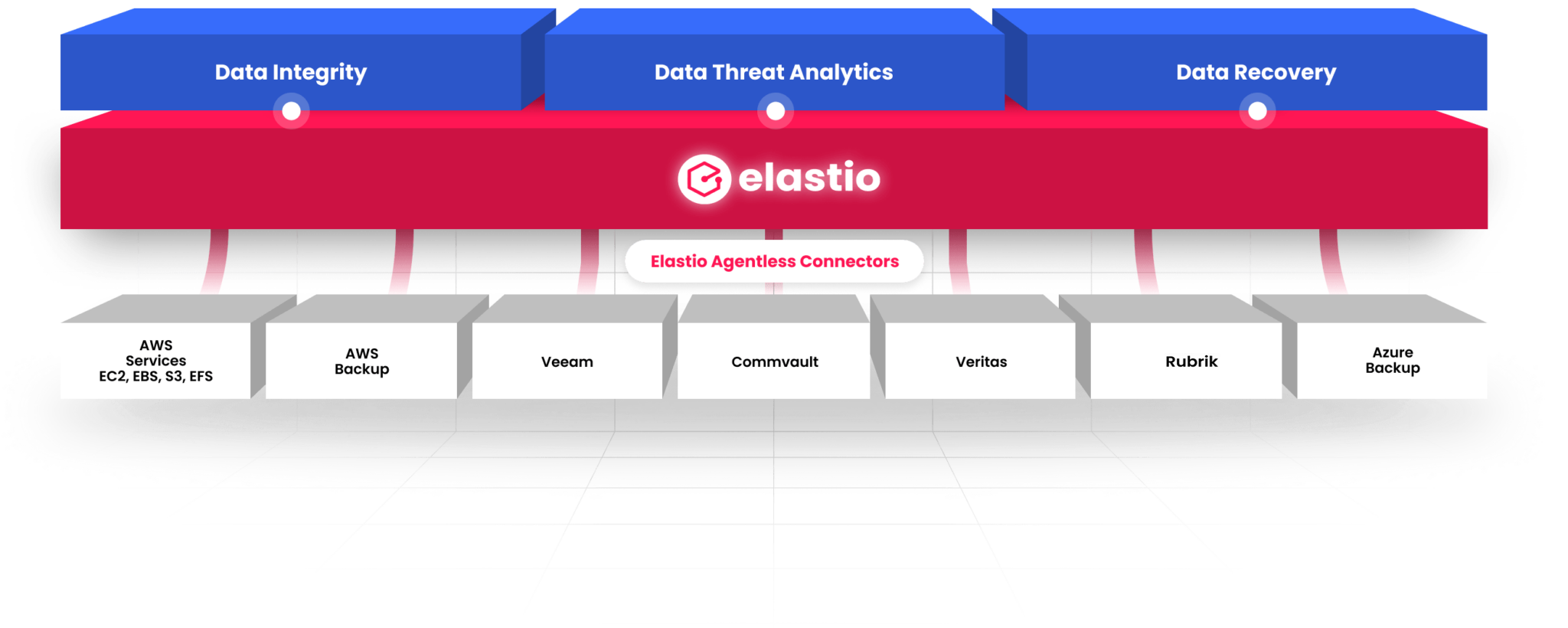
Elastio Platform
Assure your business can always recover from ransomware attacks with minimal downtime and data loss.
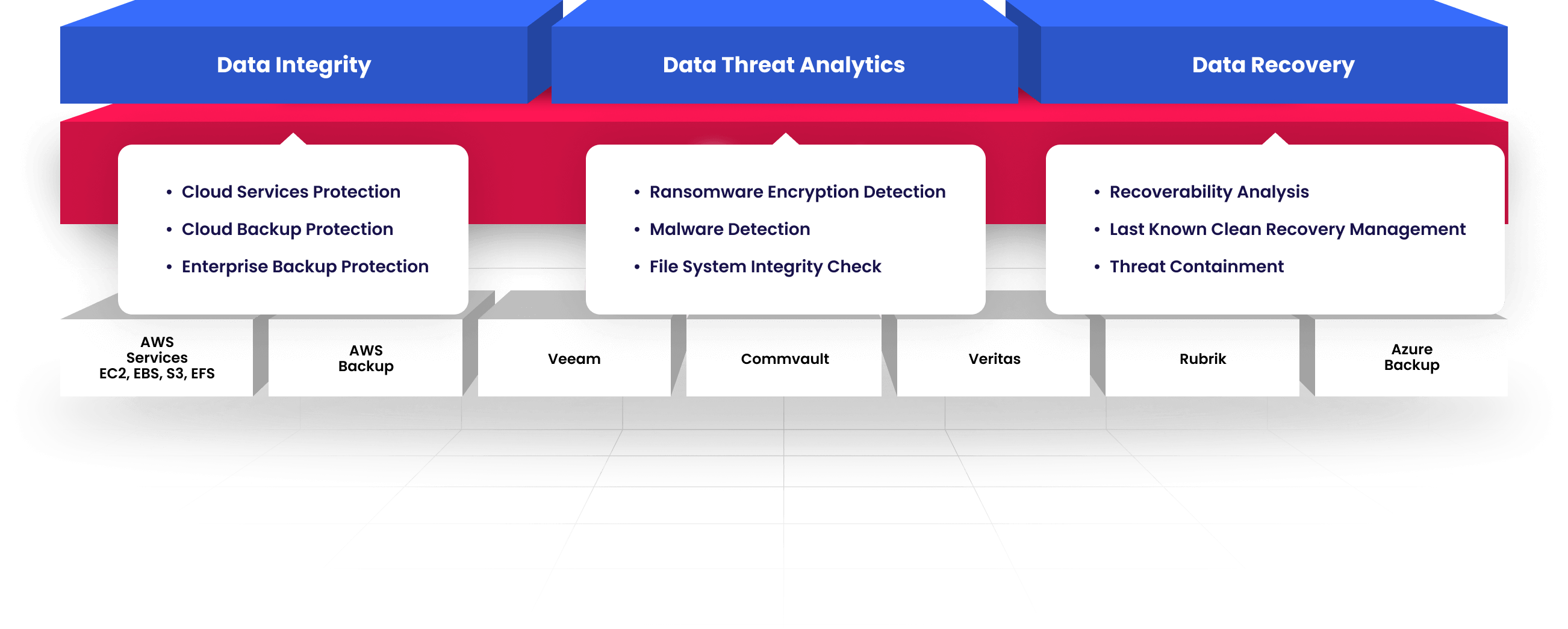
- Cloud Services Protection
- Cloud Backup Protection
- Enterprise Backup Protection
- Ransomware Encryption Detection
- Malware Detection
- File System Integrity Detection
- Recoverability Analysis
- Last Known Clean Recovery Management
- Threat Containment
Elastio Platform
Assure your business can always recover from ransomware attacks with minimal downtime and data loss.
- Cloud Services Protection
- Cloud Backup Protection
- Enterprise Backup Protection
- Ransomware Encryption Detection
- Malware Detection
- File System Integrity Detection
- Recoverability Analysis
- Last Known Clean Recovery Management
- Threat Containment
Platform Capabilities

Cloud-Native Achitecture
Scales-out based on data size, scales-up on demand for concurrent data access, and automatically scales-to-zero when jobs complete.
Scale-Out Backup Connector
Elastio scales to meet backup workloads and perform inspections with built-in queuing and scan worker management.
Agentless Side-Scanning
Elastio’s agentless approach operates outside of the production workload, ensuring it cannot be bypassed by threat actors without affecting performance.
No Production Impact
Performs deep-file inspections on offline snapshots without affecting performance of production workloads.
Optimized for Speed
Elastio inspections are optimized for speed and process half a million files in 10 minutes.
Efficient Data Management
Inspections occur without data re-hydration, speeding up inspections and lowering costs. Incremental inspections also assure cost optimizations.
Easy Deployment
Deploys in minutes and inspects immediately for fast-time-to-value.
Role-Based Access Control
Elastio offers a simple, manageable approach to Tenant access management that is less error-prone than individually assigning user permissions.
Full Data Custody
Data never moves out of your network, during or after the inspection. Only metadata appears in the Elastio console.
Platform Component Capabilities

Inspects Live Data
When other defenses fail, Elastio detects ransomware encryption in your data early to stop the spread.
Detects Ransomware Encryption
RansomwareIQ detects ransomware encryption in your live data and backups with 99.99% accuracy.
Last-Known Clean
Automatically directs you to last-known clean copy of your data for quick restoration with minimal downtime and data loss.
Inspects Backups
Backups are key to post-attack recovery. Elastio assures you always have a clean recovery point to minimize downtime and data loss. Supports most major backup providers.
Enterprise-Grade Malware Protection
Inspects live data and backups for malware, performing deep-file inspections without affecting production workloads.
Ransomware Recovery Point Objective
Ransomware Recovery Point Objective (R-RPO) reports assure your business is always in the know about potential post-attack data loss.
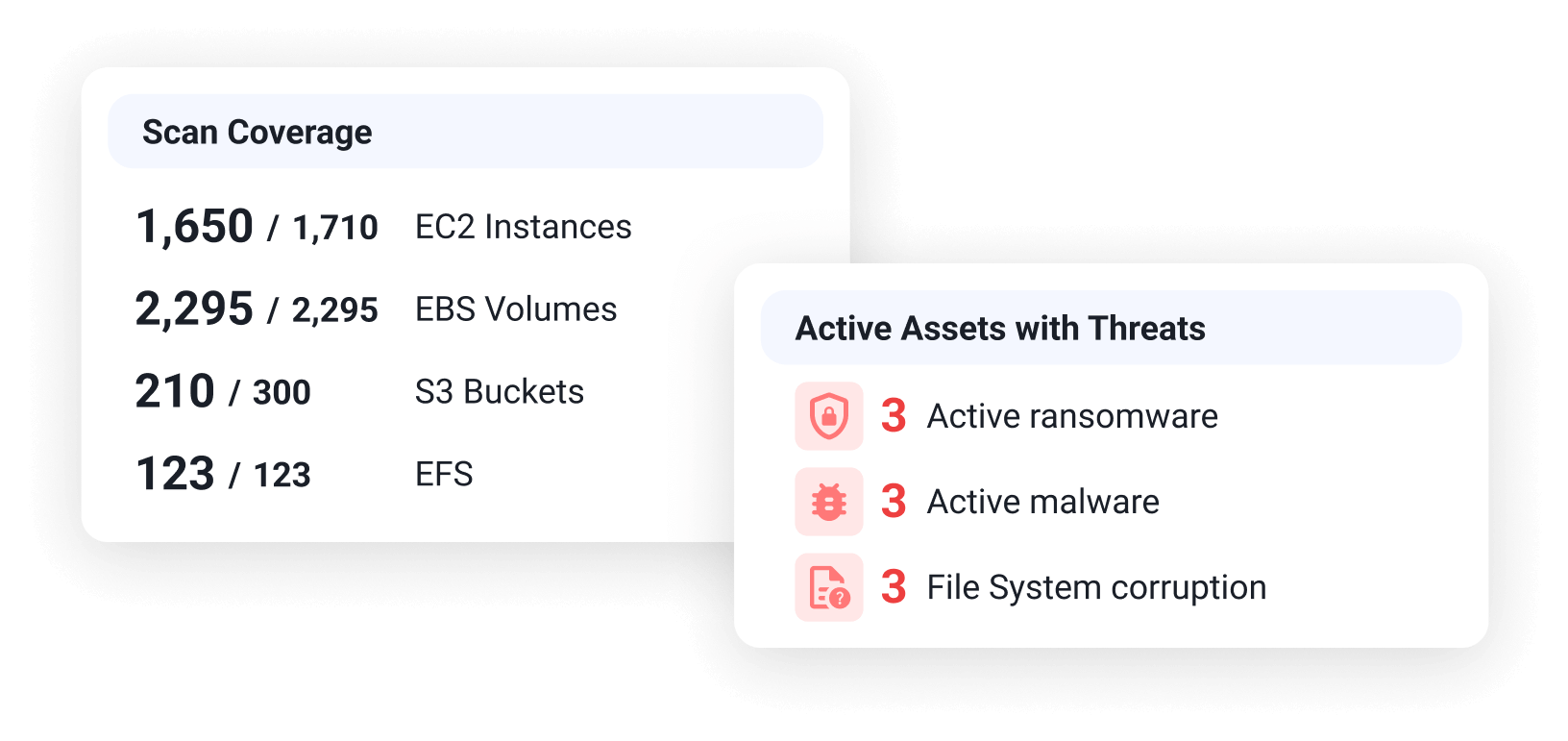
Broad AWS Service Coverage
Protects EC2, EFS, EBS, ECS, EKS, Marketplace AMIs and S3 data for a comprehensive view across your AWS data.
Alerting
Detailed alerts about the scope of the attack with actionable insights for threat remediation.
Reporting
Fully automates compliance reporting with history of inspections and threats in your data, suitable for internal leadership and external government agencies.
Auto-Detects Backups
Automatically picks up backups upon creation by backup provider and performs inspection without any user intervention.
Incident Response Team
Elastio incident response team proactively monitors your alerts and validates every finding.
Sandbox Restores
Restore infected files to a sandbox environment for forensic analysis.
Native APIs
Leverages supported Backup Providers’ native APIs to inventory, filter and inspect backups.
Integrates with your SIEM
Get alerts on Elastio findings pushed into any SIEM or ticketing solution that you use.
Fast Threat Containment
Detailed threat information, down to which individual files are infected with which ransomware variant, enables fast threat containment.
Integrates with VMWare vCenter and vCloud Director
Integrates with the central management utilities for VMWare.
Dashboarding
Customizable dashboard give customers a comprehensive view of ransomware risk across their whole environment – from a single console.
Recovery Testing
Ensure your business is prepared to recover for ransomware scenarios. Fully supports AWS Backup restore test capability for EC2, EBS, EFS and S3.
AWS Services Coverage

EC2
Elastio continuously inspects AWS EC2 workloads, including all attached EBS volumes, for ransomware encryption and malware, ensuring real-time threat detection and mitigation to protect critical business applications from disruptions. Elastio’s inspections also cover ephemeral instances, leaving no gaps in your EC2 instances. Choose between full and incremental inspections to suit your security needs.

EBS
Elastio continuously inspects AWS EBS volumes for ransomware encryption and malware in real-time.
Our solution has no volume size limit and includes inspections for unattached volumes, ensuring comprehensive coverage and eliminating security gaps.

EFS
Elastio provides continuous inspection of AWS EFS for ransomware encryption and malware, protecting file storage from compromise.
It can inspect existing files or new files incrementally, specific paths, or the full filesystem based on security needs, ensuring the availability and integrity of critical business data.

S3
Learn More

ECS/EKS
Elastio continuously protects EKS and ECS clusters, inspecting their EC2 instances and persistent EBS volumes for ransomware encryption and malware. This ensures real-time threat detection and mitigation, safeguarding critical container applications from disruptions.
AWS Marketplace Appliances
Elastio continuously inspects AWS Marketplace appliances for ransomware encryption and malware, protecting against ransomware entry via third-party applications and the ransomware encryption of critical application files.

AWS Snapshots
Elastio inspects AWS snapshots for ransomware encryption and malware, detecting threats early in its associated EBS storage and EC2 instances. It integrates with major backup vendors’ cloud-native solutions on AWS.
Backup Provider Coverage
Elastio provides a critical layer of ransomware protection for backups with advanced and precise detection for ransomware encryption and malware.
With Elastio, your backups become the true last line of defense.
- Assure your backups are free from ransomware using the Elastio anti-ransomware protection.
- Reduce downtime and data loss from an attack
- Always have a clean copy of your data.

AWS Backup
Elastio integrates seamlessly with AWS Backup through a simple AWS Backup policy tag to provide automated inspection of EC2 and EBS recovery points. Learn more
Elastio also integrates seamlessly with AWS Backup Restore Test to inspect EC2, EBS, EFS, and S3 backups through a simple AWS Backup policy tag. Learn more

Commvault
Elastio integrates seamlessly with VMware backups in Commvault, leveraging native APIs to automatically inventory Commvault backups from ComServe servers upon creation and inspect them for ransomware encryption and malware without user intervention. With Elastio you will always know what the last clean copy of your data is at any point. Learn more

Veeam
Elastio integrates with Veeam backups on VMware and AWS, leveraging native APIs to automatically inventory Veeam backups from VBR upon creation and inspect them for ransomware encryption and malware wwithout changing your current backup processes. With Elastio you will always know what the last clean copy of your data is at any point. Learn more

Veritas NetBackup
Elastio integrates with Veritas NetBackup backups on AWS, leveraging native APIs to automatically inventory backups from the NetBackup Primary Server upon creation and inspect them for ransomware encryption and malware without user intervention. With Elastio you will always know what the last clean copy of your data is at any point. Learn more

Cohesity
Elastio integrates with Cohesity backups on VMware, leveraging native APIs to automatically inventory Cohesity backups from Cohesity upon creation and inspect them for ransomware encryption and malware without any user intervention. With Elastio you will always know what the last clean copy of your data is at any point. Learn more

Rubrik
Elastio integrates with Rubrik backups on AWS, leveraging native APIs to automatically inventory Rubrik backups from Rubrik upon creation and inspect them for ransomware encryption and malware without changing your current backup processes. With Elastio you will always know what the last clean copy of your data is at any point. Coming soon.
AI-Powered Security For Your Last Line of Defense
We enable organizations to verify data integrity in near real-time, enabling clean recovery from any attack with minimal downtime and data loss.

