Dr. Srinidhi Varadarajan, Chief Scientist, Elastio Software
Since the advent of CryptoLocker in 2013, ransomware has become a major drain on businesses, affecting their survival. With 56% of businesses hit in the last 12 months and 42% of them losing data, early detection and prevention of lateral spread represents one of the most potent defenses against ransomware.
Ransomware enters an infrastructure as part of a payload through several entry vectors. One common route in the cloud is due to security misconfigurations and unpatched software vulnerabilities in the application chain, which allows an attacker to drop a payload on the victim system. Another is via the compromise of security tokens from IAM roles. More targeted attacks combine social engineering with spear phishing against identified targets – the recent MGM and Caesar attacks. The last few years have also seen the rise of human teams coordinating attacks on a single target to get as many lateral systems as possible. The problem is prevalent enough that it is a matter of when, not if. The average payout in the last twelve months was $2M per incident.
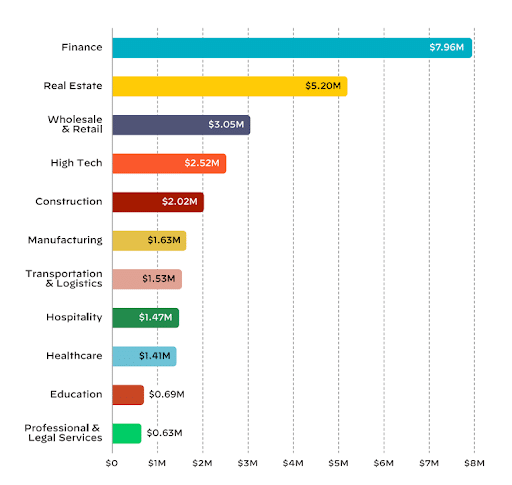
Average Ransom Demand By Industry
Ransomware is typically the last part of a larger malware payload, which includes backdoors and a communication path to command and control servers. The larger malware payload dwells for a period of time, during which it spreads laterally within the infrastructure to expand its foothold and leave further backdoors behind. In the last stage – the attack phase – a ransomware package is detonated, encrypting user data across multiple systems.
Dwell times have fallen considerably over the last year from over 72 days to 5 days for aggressive strains, which reflects the confluence of two factors. First, better cyber defenses have increased detection risk. Second, targeted attack teams are becoming more common, creating a larger initial beachhead and thus reducing the need to dwell longer than necessary. The loss of five days of data is an extinction-level event for many businesses.
Backups are commonly used to recover data encrypted during a ransomware attack. However, if the malware payload is not identified and neutered, restoring from backups simply reintroduces the backdoors from infected backups. This leads to persistent infections and a wide open exfiltration pathway within the infrastructure for repeated data ransom demands. A worse outcome occurs when malware has lingered long enough that backup retention policies rolled up old backups, leaving no clean backup that doesn’t have malware.
Clearly, backups alone are not enough – early detection of malware is needed to ensure that backups are clean and healthy. While air-gapped systems provide an additional layer of security, they are only as good as the data entering them – without early detection, malware can slip through to air-gapped backups as well.
Some backup systems deploy an anomaly detection engine to provide early warning of a ransomware attack. These engines look for signals in a snapshot, such as the change rate of the snapshot, to indicate suspicious behavior. More sophisticated engines look inside a backup to measure the entropy (degree of randomness) of files. Encrypted data is very close to the maximum measure of entropy and, intuitively, should stand out. It doesn’t – Microsoft PowerPoint files have similar entropy to encrypted files, as do many other common file formats. The issue here is the large rate of false positives that have to be sifted through even to know if there is an attack in progress. Worse yet is alert fatigue and subsequent alert suppression that misses critical patterns. As every security team can attest to, we want actionable intelligence, not another alert.
And this is just the tip of the iceberg – even sophisticated anomaly detection techniques are commonly defeated. Malware such as LockFile, Rook, BianLian encrypt subsets of data so the overall entropy remains small. Others, such as Xorist, AlphaLocker, Corona, do not change any file metadata, so signals such as the last modified time of a file remain unchanged and thus don’t trigger alerts. TimeTime encrypts files slowly over time to stay below activity threshold detectors. Alcatraz Locker uses simple file encoding, and Clop, Vaca, and several others skip encrypting the file header and thus require deep file inspection to identify their impact. The list of evasion techniques is long and continues to evolve.
Elastio addresses this problem through a two-pronged strategy – early detection in the spread phase to detect malware before it detonates and post attack recovery that quickly identifies affected data assets along with their last known clean copies. For early detection, Elastio’s data integrity engine scans every backup for known ransomware and malware strains with a database that updates continuously. This provides actionable threat intelligence that identifies the exact malware, the set of affected systems and its impact.
The post-attack recovery phase is focused on the inevitable conclusion that, however good, prevention techniques only have to fail once. Some fraction of ransomware will detonate, requiring post-attack recovery to get back to a clean state. Elastio uses an ensemble of behavioral analysis, deep file inspection, and deterministic models from our security lab to detect ransomware. Behavioral analysis identifies malicious files based on usage patterns, characteristics, and known indicators of malware. It uses a statistical model to group patterns of behavior in a high-dimensional space to determine if they are ransomware. This approach relies on the fact that all ransomware exhibits certain common characteristics in higher-order space that can be detected via statistical analysis of complex patterns. The model is very good at capturing large-scale behavior while retaining file-level granularity. The behavioral analysis also includes over-time analysis, where a timeline of backups is analyzed for the stability of their behavior over time at the granularity of each file. This technique is particularly important in de-obfuscating malware that doesn’t change metadata. Behavioral analysis can detect both known and unknown ransomware strains.
Deep file-level inspection performs a more thorough analysis of individual files to detect signs of ransomware. This approach examines the content and structure of files to identify any malicious activity or modifications that indicate ransomware encryption. By inspecting the actual data within files, it provides a higher level of accuracy in detecting ransomware attacks.
Over the last three years, Elastio’s security lab has analyzed over 1900 ransomware families and their variants, representing everything seen publicly since 2014. Some, such as Clop, have variants that are sufficiently evolved to be indistinguishable from their ancestors, including entirely different behaviors. Each malware payload with ransomware was disassembled, neutered from its command and control servers, detonated, and analyzed to produce behavior patterns and indicators of penetration. This enables a comprehensive evaluation of each ransomware threat and represents one of the most potent tools for post-attack application recovery. Over the last six months, Elastio’s security team has been analyzing as yet unreleased malware (in the wild), and the models are now refined enough that they can accurately detect the detonation of the vast majority of hitherto unseen ransomware.
Elastio operates in one of two modes. In scan-only mode, it invokes a snapshot or mounts backup from your existing backup system and scans it for malware and ransomware. It always keeps the last clean copy of backup around to ensure recovery in case of an attack. In the second mode, Elastio takes a snapshot and ingests it into a vault hosted within the customer VPC that is deduplicated, compressed, and encrypted. No data ever leaves a customer account, and for cost savings, the vault is backed by S3. The vault is immutable and uses a WORM model with no delete primitive. In this mode, Elastio additionally provides guaranteed recovery since it has the data and can ensure the provenance of the backup chain.
In both modes, the Elastio pipeline runs through three stages. The first stage involves a health check scan that ensures the base we are starting from has a clean bill of health that can be trusted. As each backup is taken, the malware detection engine scans it for early detection of unexploded malware in its spread phase. This stage produces actionable threat intelligence, including exact threat identification and its behavior. In the post attack stage, Elastio immediately identifies ransomware detonation and, more specifically, identifies the last clean copies of affected data, which can be restored to a sandbox for analysis. Post-attack recovery is complemented by direct support from Elastio’s security lab to unhook malware and rapidly return the infrastructure back to a clean state.
Our goal is simple: recover your applications when you need it most.
About Elastio
Elastio detects and precisely identifies ransomware in your data and assures rapid post-attack recovery. Our data resilience platform protects against cyber attacks when traditional cloud security measures fail.
Elastio’s agentless deep file inspection continuously monitors business-critical data to identify threats and enable quick response to compromises and infected files. Elastio provides best-in-class application protection and recovery and delivers immediate time-to-value.


